|
|
2008-06-02
, 12:03
|
|
Posts: 833 |
Thanked: 124 times |
Joined on Nov 2007
@ Based in the USA
|
#22
|
Has anyone looked into using AGPS which is coming with the WiMax version?
__________________
N810, iGo bt kb, Diablo, 10Gb storage onboard instead of a Thinkpad
OTG w/ unlimited storage!!
Put a penguin in your pocket!!
PLEASE use the Wiki
N810, iGo bt kb, Diablo, 10Gb storage onboard instead of a Thinkpad
OTG w/ unlimited storage!!
Put a penguin in your pocket!!
PLEASE use the Wiki
|
|
2008-06-02
, 15:55
|
|
Posts: 179 |
Thanked: 90 times |
Joined on Dec 2007
|
#23
|
Originally Posted by Jerome

Law Enforcement is unlikely to chase either. The MPAA could spend vast amounts of money to chase the first and gather evidence which LE may then later use(as the RIAA is for illegal music sharing). So far they have not done so. But mostly the cases you hear about are Civil not Criminal. AFIAK only one person has been prosecuted here in the states so far for hi-jacking wi-fi. And he was in his car in front of the person's house downloading child-pornography on his laptop. The owner of the AP saw him, called police and he was arrested. Hijacking wi-fi is the least of his legal (or psychological) problems.
About the police: you mean that they will go after a kid who exchanged a few movies on eMule on the basis of his i.p. and not after someone who stole a 400$ tablet?I am sure that the press will be delighted to report that if it ever happens...
Not to mention that the first scenario you mention is a federal crime. The second is a local one and police response will vary greatly from jurisdiction to jurisdiction. There are cities where even if your car is stolen, they won't send an officer to you. You'll have to go to the police station to file a report. (Which can be difficult without a car...) Is this because the police don't care? NO. It is simply Triage. In higher crime areas, violent crimes receive more attention than non-violent, major crimes more attention than minor ones...
An IP address is just a number. Proving that you received a phone call from a particular number is not the same as proving you received it from a particular person. But a picture is worth a thousand words. It is something any cop or prosecutor can wrap their brains around and doesn't take an expert witness to explain to a jury. This increases the chance of a conviction and reduces the cost of a trial...
cheers,
kernelpanic
p.s. -geminiii42, aGPS is supposedly coming with Diablo and works well. I'm trying to get a working framework up in time for that...
Last edited by kernelpanic; 2008-06-02 at 15:57. Reason: add ps
|
|
2008-06-02
, 16:09
|
|
|
Posts: 3,096 |
Thanked: 1,525 times |
Joined on Jan 2006
@ Michigan, USA
|
#24
|
I used to have a similar type of home grown scipts.
http://penguinbait.com/index.html
It would take a picture, GPS location and send back to my webserver.
It would then create some custom html to display the info. The picture used to be in the upper left corner. But when I converted to the 770 I had no camera.
I initially made this for a laptop before I purchased my 770. Then I never really did much after making it work on the 770.
So all that said, my point is perhaps this application can be two fold.
1) Yes provide picture GPS and related info when remotely enabled for security purposes.
2) Also build a CGI script for webservers that people can use to display info people could see. Sort of a walk around real time blog app. Have ability to add messages from the tablet. My wife used to use my webpage and I always had dinner ready when I got home. Also the mailman was always gone when I got home
http://penguinbait.com/index.html
It would take a picture, GPS location and send back to my webserver.
It would then create some custom html to display the info. The picture used to be in the upper left corner. But when I converted to the 770 I had no camera.
I initially made this for a laptop before I purchased my 770. Then I never really did much after making it work on the 770.
So all that said, my point is perhaps this application can be two fold.
1) Yes provide picture GPS and related info when remotely enabled for security purposes.
2) Also build a CGI script for webservers that people can use to display info people could see. Sort of a walk around real time blog app. Have ability to add messages from the tablet. My wife used to use my webpage and I always had dinner ready when I got home. Also the mailman was always gone when I got home

__________________
To all my Maemo friends. I will no longer be monitoring any of my threads here on a regular basis. I am no longer supporting anything I did under maemo at maemo.org. If you need some help with something you can reach me at tablethacker.com or www.facebook.com/penguinbait. I have disabled my PM's here, and removed myself from Council email and Community mailing list. There has been some fun times, see you around.
To all my Maemo friends. I will no longer be monitoring any of my threads here on a regular basis. I am no longer supporting anything I did under maemo at maemo.org. If you need some help with something you can reach me at tablethacker.com or www.facebook.com/penguinbait. I have disabled my PM's here, and removed myself from Council email and Community mailing list. There has been some fun times, see you around.
|
|
2008-06-02
, 16:11
|
|
|
Posts: 4,930 |
Thanked: 2,272 times |
Joined on Oct 2007
|
#25
|
kernelpanic...
Great plan; I think you're dead on about the user signing with private-key and the tablet having public-key; but I'm not sure why the server needs to authenticate? If the server is pushing messages signed with the right private-key (and hence, valid messages from the owner), isn't that good enough? Not that it hurts; just wondering why...
I'd be inclined to have arbitrary execution (as user user) through the daemon; that leaves you with the ability to wipe files, etc. at your own discretion. Also, you can then make the tablet (if you pre-equipped it with the right tools...) ssh out to your desktop, giving you a shell into your tablet when it's connected. The ability to manually fiddle around, diagnosing his network, firing up GPS and/or camera when desired (because intelligence >> heuristics), and so on, is highly valuable, imho. Streaming video and selecting which snapshot to take (and send through to the official server, for evidence purposes), you get the idea. (I won't even mention cracking all the machines on his home network, finding one with an old PCI modem still installed, and dialing out to your cell so you can get his phone number, or anything else like that.)
Zealous Autoconfig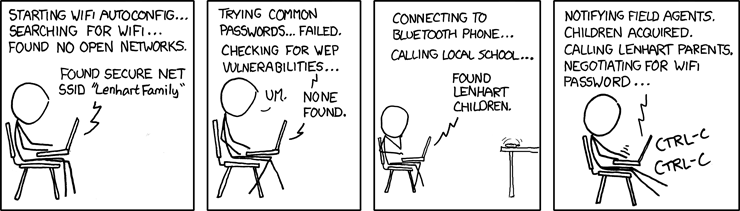
I can't be the first one who thought, upon reading "It should also try to connect aggressively to any unencrypted Internet connection it can to phone home and ignore normal WLAN connection settings also on a schedule.", that it might as well have an option to use aircrack; after all, if the cops catch up to him cracking networks with his tablet, you have a better chance of getting it back...
You obviously can't put that in an official release. But if the owner can run arbitrary code, that's their decision to add whatever level of zeal to their autoconfig they are willing to risk. (Hmmm... grab the input-method's word list to sieze credit-card numbers after netstat shows connection to online payment sites... maybe I'd better shut up before I completely throw you off this idea.) But if the daemon's open-source, people will add such functionality anyway, so it seems like it should be included.
Great plan; I think you're dead on about the user signing with private-key and the tablet having public-key; but I'm not sure why the server needs to authenticate? If the server is pushing messages signed with the right private-key (and hence, valid messages from the owner), isn't that good enough? Not that it hurts; just wondering why...
I'd be inclined to have arbitrary execution (as user user) through the daemon; that leaves you with the ability to wipe files, etc. at your own discretion. Also, you can then make the tablet (if you pre-equipped it with the right tools...) ssh out to your desktop, giving you a shell into your tablet when it's connected. The ability to manually fiddle around, diagnosing his network, firing up GPS and/or camera when desired (because intelligence >> heuristics), and so on, is highly valuable, imho. Streaming video and selecting which snapshot to take (and send through to the official server, for evidence purposes), you get the idea. (I won't even mention cracking all the machines on his home network, finding one with an old PCI modem still installed, and dialing out to your cell so you can get his phone number, or anything else like that.)
Zealous Autoconfig

I can't be the first one who thought, upon reading "It should also try to connect aggressively to any unencrypted Internet connection it can to phone home and ignore normal WLAN connection settings also on a schedule.", that it might as well have an option to use aircrack; after all, if the cops catch up to him cracking networks with his tablet, you have a better chance of getting it back...
You obviously can't put that in an official release. But if the owner can run arbitrary code, that's their decision to add whatever level of zeal to their autoconfig they are willing to risk. (Hmmm... grab the input-method's word list to sieze credit-card numbers after netstat shows connection to online payment sites... maybe I'd better shut up before I completely throw you off this idea.) But if the daemon's open-source, people will add such functionality anyway, so it seems like it should be included.
__________________
World's first inductively-charged N900!
World's first inductively-charged N900!
|
|
2008-06-02
, 17:40
|
|
Posts: 373 |
Thanked: 56 times |
Joined on Dec 2005
@ Ottawa, ON
|
#26
|
Originally Posted by tme

I like this idea. Combine it with the verification that the script is GPG signed before executing it and it would work nicely in a decentralized private server environment as well as some centralized service for those without access to a webserver.
I while ago I started putting together my own tracking package but never finished
it because my tablet has not been stolen yet. The basic premise was:
1. upon connection to internet, retrieve a specific file from my webserver. the
request may include nearby wifi router macs.
2. if the file retrieves ok, execute it
this is very simple and means i can do the rest of the implementation
later if needed.
the webserver logs the ip address and router macs. the macs' location can be
looked up (eg: on wigle.net).
normally, my webserver will just fail the request. if i lose my tablet, i
can place a suitable script on the server. an example script might set up a
tunnel back to my pc so that i can ssh into the tablet and do gps logs, delete
files, camera capture etc, even behind a firewall.
Please publish your recovery script and method of linking the wget script into the wifi initialization if you do pursue this.
|
|
2008-06-02
, 19:31
|
|
Posts: 179 |
Thanked: 90 times |
Joined on Dec 2007
|
#27
|
Originally Posted by Benson

2 reasons-
kernelpanic...
Great plan; I think you're dead on about the user signing with private-key and the tablet having public-key; but I'm not sure why the server needs to authenticate? If the server is pushing messages signed with the right private-key (and hence, valid messages from the owner), isn't that good enough? Not that it hurts; just wondering why...
1. web of trust- The user public keys can be signed by the server. Adding another barrier to unauthorized remote code execution.
2. Encryption- Data sent to the server can be encrypted (in case on wanted to retrieve important documents prior to wiping them remotely.
I'd be inclined to have arbitrary execution (as user user) through the daemon; that leaves you with the ability to wipe files, etc. at your own discretion. Also, you can then make the tablet (if you pre-equipped it with the right tools...) ssh out to your desktop, giving you a shell into your tablet when it's connected. The ability to manually fiddle around, diagnosing his network, firing up GPS and/or camera when desired (because intelligence >> heuristics), and so on, is highly valuable, imho. Streaming video and selecting which snapshot to take (and send through to the official server, for evidence purposes), you get the idea. (I won't even mention cracking all the machines on his home network, finding one with an old PCI modem still installed, and dialing out to your cell so you can get his phone number, or anything else like that.)
 )
) BTW does anyone know if osso-gnupg includes gpgme?
I can't be the first one who thought, upon reading "It should also try to connect aggressively to any unencrypted Internet connection it can to phone home and ignore normal WLAN connection settings also on a schedule
You obviously can't put that in an official release.
The Computer Fraud and Abuse Act states that it's illegal to access protected (i.e. encrypted) networks/systems. There ARE States with more restrictive laws including(but certainly not limited to)- Texas, Michigan, Florida, Illinois, Washington, and Alaska.
For example in Texas it's illegal to access ANY network without permission.
I'll likely do exactly as Bill Gates and put in the option in but leave it 'off' by default. I'll also add a popup that warns the user to check the applicable laws in their Country/State/Whatever... (Note- Windows doesn't do that even though one could get into lot's of hot water unintentionally in the States listed above. And Microsoft is based in one of those states!!?)
But if the owner can run arbitrary code, that's their decision to add whatever level of zeal to their autoconfig they are willing to risk.
But if the daemon's open-source, people will add such functionality anyway, so it seems like it should be included.
Also, open-sourcing is to allow scrutiny of the security model to prevent abuse. I'll likely also have some kind of signature on the binary that users actually install on-tablet. So that way, at least if someone subverts the daemon, they can't then use the main server for their nastiness... (In Fact- Make that reason #3 for the server to have a key also.)
cheers,
kernelpanic
Last edited by kernelpanic; 2008-06-02 at 19:34. Reason: spelling
|
|
2008-06-02
, 19:39
|
|
Posts: 477 |
Thanked: 118 times |
Joined on Dec 2005
@ Munich, Germany
|
#28
|
Originally Posted by kernelpanic


Law Enforcement is unlikely to chase either. The MPAA could spend vast amounts of money to chase the first and gather evidence which LE may then later use(as the RIAA is for illegal music sharing). So far they have not done so.
I think the RIAA has tried, see:
http://epic.org/privacy/copyright/verizon/
Mostly, they have not won, see:
http://recordingindustryvspeople.blo...alifornia.html
http://arstechnica.com/news.ars/post/20060713-7257.html
but in both cases above, they got the name of the person who paid for the i.p. address... which is all you need here. Then a search warrant.
|
|
2008-06-02
, 20:52
|
|
|
Posts: 4,930 |
Thanked: 2,272 times |
Joined on Oct 2007
|
#29
|
Originally Posted by kernelpanic

Sounds good, although I had been assuming the owner's public key would be transferred to the tablet directly by the owner. (#1 seems to run on the assumption that key distribution is through the server, which is also fine.)
2 reasons-
1. web of trust- The user public keys can be signed by the server. Adding another barrier to unauthorized remote code execution.
2. Encryption- Data sent to the server can be encrypted (in case on wanted to retrieve important documents prior to wiping them remotely.
Some kind of port-knocking handshake to set-up ssh into the stolen tablet would be great. I really like the feature ideas everyone is coming up with. Most of them would be trivial to add to a working app. I've actually started coding the daemon. But first I'm trying to ensure that any implementation I come up with is secure. (There's too many insecure implementations of secure algorithms out there already esp. on Debian)
The ability to function asynchronously also permits drive-by operations; I drive past a couple of APs strong enough that I can connect and load a single web page before I lose them; those connections would be worthless for ssh, but excellent for the tablet to receive instructions. (And that could be instrumental, in the case where the thief has an encrypted AP, or perhaps no AP at all, in the locations the tablet usually holds still.)
Still, your approach is certainly the correct; security, then functionality, then features. There's a lot that could go wrong if this were approached out-of-order.
I think I can actually. Is this any different than the 'Automatically Connect to non-preferred Networks' setting in windows XP? That setting causes XP to automatically connect to any unencrypted WLAN it finds. the sauce that suits the goose...
The Computer Fraud and Abuse Act states that it's illegal to access protected (i.e. encrypted) networks/systems. There ARE States with more restrictive laws including(but certainly not limited to)- Texas, Michigan, Florida, Illinois, Washington, and Alaska.
For example in Texas it's illegal to access ANY network without permission.
I'll likely do exactly as Bill Gates and put in the option in but leave it 'off' by default. I'll also add a popup that warns the user to check the applicable laws in their Country/State/Whatever... (Note- Windows doesn't do that even though one could get into lot's of hot water unintentionally in the States listed above. And Microsoft is based in one of those states!!?)
Putting SSH access in seems like enough to me. Then the owner can do whatever they want. But THEY have to do it. Having the app automatically do questionable or illegal things is not my goal.
Also, open-sourcing is to allow scrutiny of the security model to prevent abuse. I'll likely also have some kind of signature on the binary that users actually install on-tablet. So that way, at least if someone subverts the daemon, they can't then use the main server for their nastiness... (In Fact- Make that reason #3 for the server to have a key also.)
That description could mean that the client would be open-source for verification, but the server would refuse to communicate with any but official binaries -- I doubt that this was your intent, but if so, I'll be happy to write a full-page rant explaining why this is bad, without resorting to RMS-style moral arguments. (Starring Ken's back-door, of course.)
__________________
World's first inductively-charged N900!
World's first inductively-charged N900!
|
|
2008-06-02
, 21:12
|
|
Posts: 179 |
Thanked: 90 times |
Joined on Dec 2007
|
#30
|
Originally Posted by Jerome

That's why I said "as the RIAA has"
I think the RIAA has tried, see:
http://epic.org/privacy/copyright/verizon/
In the case of a minor property crime it'll take more time and money than a $400 tablet is worth to go that route.
PROGRESS REPORT- I've successfully compiled a full version of GnuPG and GPGme in scratchbox. (osso-gnupg is fairly useless) In order to actually get them onto the tablet I'll have to build an empty osso-gnupg package with no deps or conflicts, then install gnupg and gpgme, then build another osso-gnupg which depends on gnupg instead of conflicting with it and install that. I should be done with that this afternoon. (Really that's only necessary for the device though. I've already got them installed in scratchbox.)
Then Ive got to actually learn the gpgme lib as I've never used it

But things are progressing faster than I'd thought as most of what I need *is* available in libraries.
The other thing I was thinking is if we're going to use the full GnuPG on the device, we can generate the key there and tell the user to copy it off of the tablet. Then, if recovery is needed only the signing of the request message needs to be done in the browser/java-script code...
cheers,
kernelpanic








it because my tablet has not been stolen yet."
tme, I will steal your tablet so you will finish the app.