| The Following 3 Users Say Thank You to Halftux For This Useful Post: | ||
|
|
2016-05-14
, 20:52
|
|
|
Posts: 868 |
Thanked: 2,516 times |
Joined on Feb 2012
@ Germany
|
#82
|
USB LAN Connection Windows 7 Internet to N900
Prerequirements usb lan:
[PC]
driver e.g. from madde
Connect a windows system with usb lan
Now the N900 should have an ip 192.168.137.XXX and the tmp resolv should have domain mshome.net and nameserver 192.168.137.1 entry. It could be that some apps need a dummy connection.
Disconnecting:
Last edited by Halftux; 2016-05-15 at 07:47. Reason: added disconnecting
Prerequirements usb lan:
[PC]
driver e.g. from madde
Connect a windows system with usb lan
- [N900] connect to internet wifi/gprs/bt-pan
- [N900] genwall {route-usb} click module button and load Windows module
- [N900-PC] connect the usb cable (PC Suite-Modus)
- [PC] run ncpa.cpl then properties from internet network device, sharing, activate ics and choose network from N900 usb lan.
- [N900] genwall {route-ipinfo} click dhclient usb0, ok
Now the N900 should have an ip 192.168.137.XXX and the tmp resolv should have domain mshome.net and nameserver 192.168.137.1 entry. It could be that some apps need a dummy connection.
Disconnecting:
- [N900] disconnect dummy network
- [N900-PC] disconnect the usb cable
- [N900] genwall {route-usb} click stop button
- [N900] genwall {route-gate} reset tmp resolv
__________________
N900: gpxsee, fahrplan, gpscon, genwall, qrcode, hextool, libjansson4, libevent-2.0-5, cnee, psi-plus, mihphoto, shc
Maemo flasher/rescue live image.
Fremantle Harmattan SDK VM
N900: gpxsee, fahrplan, gpscon, genwall, qrcode, hextool, libjansson4, libevent-2.0-5, cnee, psi-plus, mihphoto, shc
Maemo flasher/rescue live image.
Fremantle Harmattan SDK VM
Last edited by Halftux; 2016-05-15 at 07:47. Reason: added disconnecting
|
|
2019-03-10
, 18:25
|
|
|
Posts: 868 |
Thanked: 2,516 times |
Joined on Feb 2012
@ Germany
|
#84
|
Genwall is available for SFOS too now.
https://openrepos.net/content/halftux/genwall-0
It has not so many functions at the moment because many hacks were specific for the N900/maemo device. Hence it is based on version 1.0.2.
On my Jolla C I have following iptable rules as a standard. The funny thing is, they were all as double roule so I guess they were set twice and they belong to mobile internet.
I created under [local]--[Settings] a checkbox include drop SSDP on WWAN. When this checkbox is enabled the same rules will be created in the script but only once.
The [local]--[ssh] tab is not optimal at the moment. When there is no network the process takes unusual long don't know why, maybe I need to open an own process for it.
You can also try the command in your console if you like.
Thats it have fun.
https://openrepos.net/content/halftux/genwall-0
It has not so many functions at the moment because many hacks were specific for the N900/maemo device. Hence it is based on version 1.0.2.
On my Jolla C I have following iptable rules as a standard. The funny thing is, they were all as double roule so I guess they were set twice and they belong to mobile internet.
Chain OUTPUT (policy ACCEPT 132K packets, 12M bytes)
num pkts bytes target prot opt in out source destination
1 0 0 DROP udp -- * rmnet_data7 0.0.0.0/0 0.0.0.0/0 udp dpt:1900 /* Drop SSDP on WWAN */
2 0 0 DROP udp -- * rmnet_data6 0.0.0.0/0 0.0.0.0/0 udp dpt:1900 /* Drop SSDP on WWAN */
3 0 0 DROP udp -- * rmnet_data5 0.0.0.0/0 0.0.0.0/0 udp dpt:1900 /* Drop SSDP on WWAN */
4 0 0 DROP udp -- * rmnet_data4 0.0.0.0/0 0.0.0.0/0 udp dpt:1900 /* Drop SSDP on WWAN */
5 0 0 DROP udp -- * rmnet_data3 0.0.0.0/0 0.0.0.0/0 udp dpt:1900 /* Drop SSDP on WWAN */
6 0 0 DROP udp -- * rmnet_data2 0.0.0.0/0 0.0.0.0/0 udp dpt:1900 /* Drop SSDP on WWAN */
7 0 0 DROP udp -- * rmnet_data1 0.0.0.0/0 0.0.0.0/0 udp dpt:1900 /* Drop SSDP on WWAN */
8 0 0 DROP udp -- * rmnet_data0 0.0.0.0/0 0.0.0.0/0 udp dpt:1900 /* Drop SSDP on WWAN */
9 0 0 DROP udp -- * rmnet_data7 0.0.0.0/0 0.0.0.0/0 udp dpt:1900 /* Drop SSDP on WWAN */
10 0 0 DROP udp -- * rmnet_data6 0.0.0.0/0 0.0.0.0/0 udp dpt:1900 /* Drop SSDP on WWAN */
11 0 0 DROP udp -- * rmnet_data5 0.0.0.0/0 0.0.0.0/0 udp dpt:1900 /* Drop SSDP on WWAN */
12 0 0 DROP udp -- * rmnet_data4 0.0.0.0/0 0.0.0.0/0 udp dpt:1900 /* Drop SSDP on WWAN */
13 0 0 DROP udp -- * rmnet_data3 0.0.0.0/0 0.0.0.0/0 udp dpt:1900 /* Drop SSDP on WWAN */
14 0 0 DROP udp -- * rmnet_data2 0.0.0.0/0 0.0.0.0/0 udp dpt:1900 /* Drop SSDP on WWAN */
15 0 0 DROP udp -- * rmnet_data1 0.0.0.0/0 0.0.0.0/0 udp dpt:1900 /* Drop SSDP on WWAN */
16 0 0 DROP udp -- * rmnet_data0 0.0.0.0/0 0.0.0.0/0 udp dpt:1900 /* Drop SSDP on WWAN */
I created under [local]--[Settings] a checkbox include drop SSDP on WWAN. When this checkbox is enabled the same rules will be created in the script but only once.
The [local]--[ssh] tab is not optimal at the moment. When there is no network the process takes unusual long don't know why, maybe I need to open an own process for it.
You can also try the command in your console if you like.
Code:
lsof -i | egrep '(COMMAND|sshd)'
__________________
N900: gpxsee, fahrplan, gpscon, genwall, qrcode, hextool, libjansson4, libevent-2.0-5, cnee, psi-plus, mihphoto, shc
Maemo flasher/rescue live image.
Fremantle Harmattan SDK VM
N900: gpxsee, fahrplan, gpscon, genwall, qrcode, hextool, libjansson4, libevent-2.0-5, cnee, psi-plus, mihphoto, shc
Maemo flasher/rescue live image.
Fremantle Harmattan SDK VM
| The Following User Says Thank You to Halftux For This Useful Post: | ||
|
|
2019-04-03
, 18:33
|
|
|
Posts: 868 |
Thanked: 2,516 times |
Joined on Feb 2012
@ Germany
|
#85
|
New version released for SFOS.
v1.1.0-1
- added filter list for deleting rules
- fixed addnow ports dialog
- added rules creator from log
- added ofono info
- added iptables log option and view
- added messages
With the new added features you can add and remove rules during runtime. I will try to explain how....
First you need to generate your rules again with a checked checkbox "activate logging for Rejectwall". After that you need to run the script.

Then you try to connect with your pc to a closed port. In this example I used ftp 21 to generate some kernel messages.
For an easy readability I would suggest to set an filter on the log list entry names. When you would like to add a rule then I would suggest following filter settings.
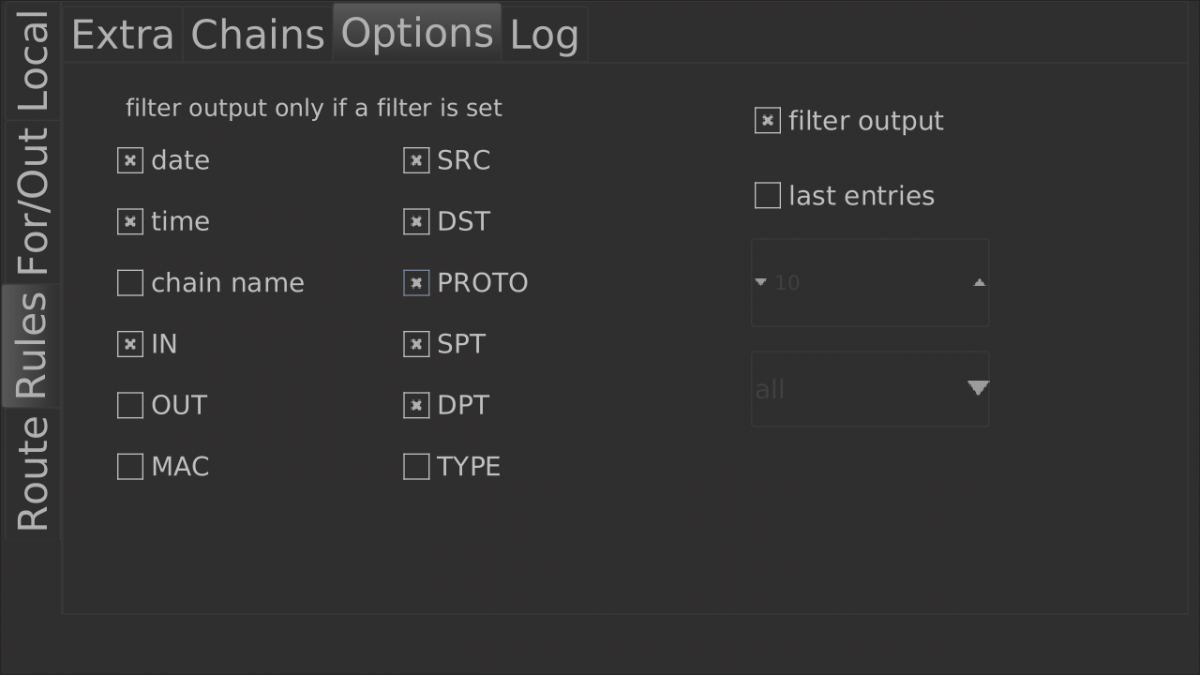
When you are play with outgoing packages, you need to choose out instead of in.
After the filter is set go to the rules--chains tab again and choose as "filter log" Rejectwall and hit the load button.
Then you will get filtered kernel messages to the log textedit. In the right top corner there will be a menu button. There you could choose "open" to open a listwidget. Now you could choose a rejected event and the rules creator pops up.
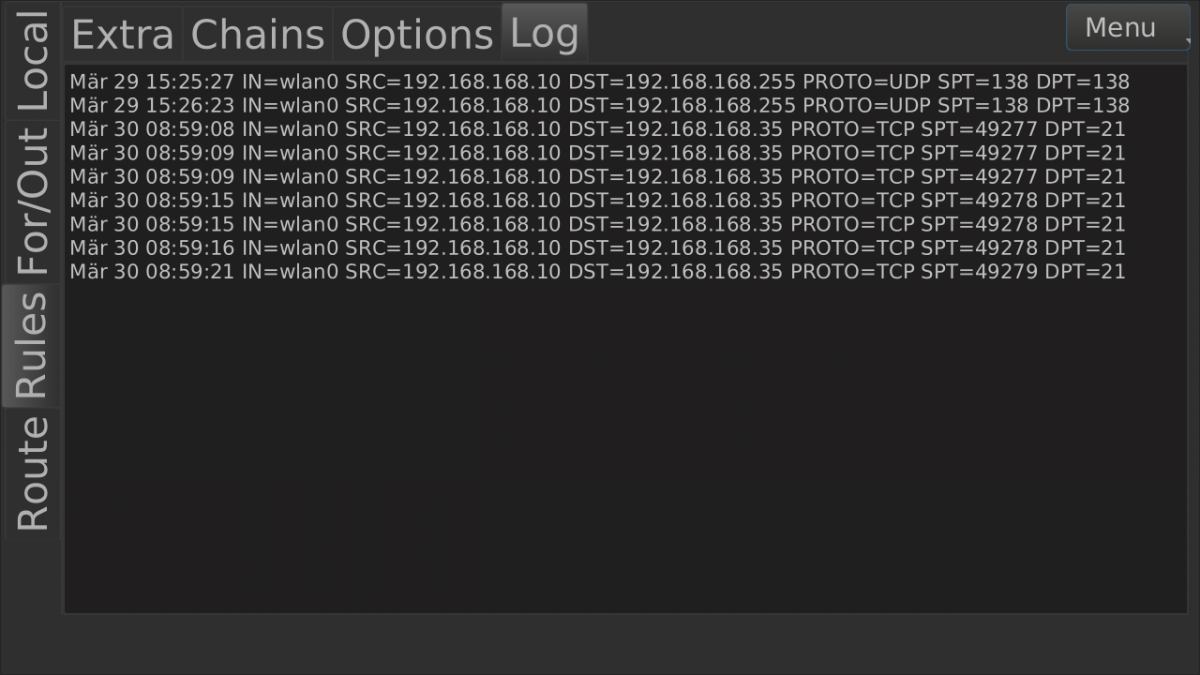
The rules creator can create some different rules for you, which will be added in the listwidget on the rules--extra tab. With the current ip checkbox, when activated, you could restrict the rule to the source ip.
With accept and drop button you create the rule. You can also drop the packages into the firewall chain. When you don't like the source ip you could also drop all incoming from that ip with "drop all from ip".
The accept now button will open promptly the port ristricted to an ip or not depends on the checkbox.
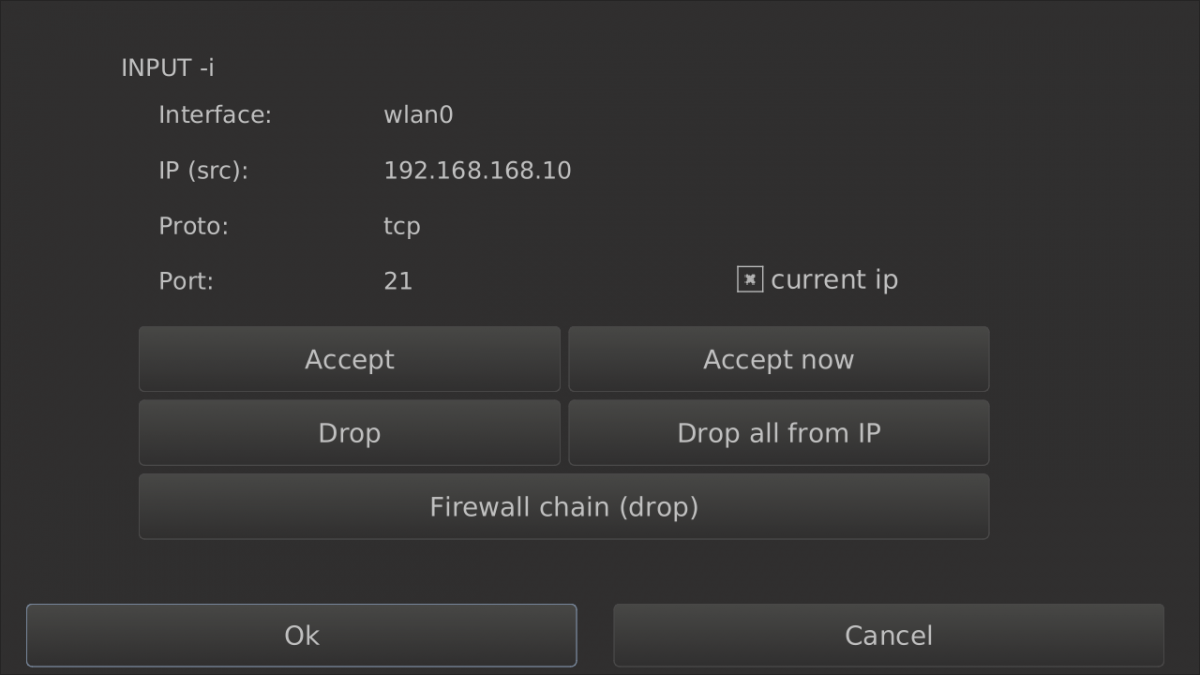
Now for example when you would like to close the port again you could go to the local--filter tab, there is again a menu button, where you choose Input. A listwidget will open, there you select the specific rule and by pushing the delete button it will be promptly removed.
There is also another way to open a port during runtime.
Under local--ports tab you will find the add now button. Set you port and then hit the button. Now you will see how many rules are in Input. Here you could choose a rule number for adding. Be careful with choosing not that the rule has no effect. When you use add now from the log filter, the generated rule has everytime number one.
Choose the interface and push the insert button.
Another thing, I also implemented some ofono modem and sim card information. There are some abbreviations for which I write the full name here.
LAC= Location Area Code
CID= Cell Id
MCC= Mobile Country Code
MNC= Mobile Network Code
v1.1.0-1
- added filter list for deleting rules
- fixed addnow ports dialog
- added rules creator from log
- added ofono info
- added iptables log option and view
- added messages
With the new added features you can add and remove rules during runtime. I will try to explain how....
First you need to generate your rules again with a checked checkbox "activate logging for Rejectwall". After that you need to run the script.

Then you try to connect with your pc to a closed port. In this example I used ftp 21 to generate some kernel messages.
For an easy readability I would suggest to set an filter on the log list entry names. When you would like to add a rule then I would suggest following filter settings.

When you are play with outgoing packages, you need to choose out instead of in.
After the filter is set go to the rules--chains tab again and choose as "filter log" Rejectwall and hit the load button.
Then you will get filtered kernel messages to the log textedit. In the right top corner there will be a menu button. There you could choose "open" to open a listwidget. Now you could choose a rejected event and the rules creator pops up.

The rules creator can create some different rules for you, which will be added in the listwidget on the rules--extra tab. With the current ip checkbox, when activated, you could restrict the rule to the source ip.
With accept and drop button you create the rule. You can also drop the packages into the firewall chain. When you don't like the source ip you could also drop all incoming from that ip with "drop all from ip".
The accept now button will open promptly the port ristricted to an ip or not depends on the checkbox.

Now for example when you would like to close the port again you could go to the local--filter tab, there is again a menu button, where you choose Input. A listwidget will open, there you select the specific rule and by pushing the delete button it will be promptly removed.
There is also another way to open a port during runtime.
Under local--ports tab you will find the add now button. Set you port and then hit the button. Now you will see how many rules are in Input. Here you could choose a rule number for adding. Be careful with choosing not that the rule has no effect. When you use add now from the log filter, the generated rule has everytime number one.
Choose the interface and push the insert button.
Another thing, I also implemented some ofono modem and sim card information. There are some abbreviations for which I write the full name here.
LAC= Location Area Code
CID= Cell Id
MCC= Mobile Country Code
MNC= Mobile Network Code
__________________
N900: gpxsee, fahrplan, gpscon, genwall, qrcode, hextool, libjansson4, libevent-2.0-5, cnee, psi-plus, mihphoto, shc
Maemo flasher/rescue live image.
Fremantle Harmattan SDK VM
N900: gpxsee, fahrplan, gpscon, genwall, qrcode, hextool, libjansson4, libevent-2.0-5, cnee, psi-plus, mihphoto, shc
Maemo flasher/rescue live image.
Fremantle Harmattan SDK VM
| The Following 2 Users Say Thank You to Halftux For This Useful Post: | ||
|
|
2019-04-04
, 09:51
|
|
|
Posts: 868 |
Thanked: 2,516 times |
Joined on Feb 2012
@ Germany
|
#87
|
Originally Posted by lantern

No Aliens and Androids on my phone
As a suggestion,would be awesome to have it parse uids of installed android apps and block/enable internet access for them by theirs uid.

So it would be nice if somebody could attach the file where the uids get saved and also tell me the location (full path).
__________________
N900: gpxsee, fahrplan, gpscon, genwall, qrcode, hextool, libjansson4, libevent-2.0-5, cnee, psi-plus, mihphoto, shc
Maemo flasher/rescue live image.
Fremantle Harmattan SDK VM
N900: gpxsee, fahrplan, gpscon, genwall, qrcode, hextool, libjansson4, libevent-2.0-5, cnee, psi-plus, mihphoto, shc
Maemo flasher/rescue live image.
Fremantle Harmattan SDK VM
| The Following User Says Thank You to Halftux For This Useful Post: | ||
|
|
2019-04-04
, 12:14
|
|
|
Posts: 4,118 |
Thanked: 8,901 times |
Joined on Aug 2010
@ Ruhrgebiet, Germany
|
#88
|
info: https://android.stackexchange.com/qu...ication-stored
/opt/alien/data/system/packages.xml
seems to hold all info and also every single right
/opt/alien/data/system/packages.list
more simple list with names and uids
ad 1: if this is the base where each application gets its rights from at start then it should not be so hard to implement a GUI for SEDing this xml, or? (android noob )
)
/opt/alien/data/system/packages.xml
seems to hold all info and also every single right
/opt/alien/data/system/packages.list
more simple list with names and uids
ad 1: if this is the base where each application gets its rights from at start then it should not be so hard to implement a GUI for SEDing this xml, or? (android noob
 )
)
__________________
SIM-Switcher, automated SIM switching with a Double (Dual) SIM adapter
--
Thank you all for voting me into the Community Council 2014-2016!
Please consider your membership / supporting Maemo e.V. and help to spread this by following/copying this link to your TMO signature:
[MC eV] Maemo Community eV membership application, http://talk.maemo.org/showthread.php?t=94257
editsignature, http://talk.maemo.org/profile.php?do=editsignature
SIM-Switcher, automated SIM switching with a Double (Dual) SIM adapter
--
Thank you all for voting me into the Community Council 2014-2016!
Please consider your membership / supporting Maemo e.V. and help to spread this by following/copying this link to your TMO signature:
[MC eV] Maemo Community eV membership application, http://talk.maemo.org/showthread.php?t=94257
editsignature, http://talk.maemo.org/profile.php?do=editsignature
| The Following 3 Users Say Thank You to peterleinchen For This Useful Post: | ||
|
|
2024-08-08
, 10:48
|
|
Posts: 109 |
Thanked: 150 times |
Joined on May 2012
|
#89
|
Apologies for necroposting, i was wondering: the N9 version doesn't run on stock kernel, does it?
|
|
2024-08-09
, 20:02
|
|
|
Posts: 868 |
Thanked: 2,516 times |
Joined on Feb 2012
@ Germany
|
#90
|
As far as I can remember it runs on stock kernel but you need to load the stock iptables kernel modules. But they have a very limited functionality.
So for full support you need to use kernel plus.
So for full support you need to use kernel plus.
__________________
N900: gpxsee, fahrplan, gpscon, genwall, qrcode, hextool, libjansson4, libevent-2.0-5, cnee, psi-plus, mihphoto, shc
Maemo flasher/rescue live image.
Fremantle Harmattan SDK VM
N900: gpxsee, fahrplan, gpscon, genwall, qrcode, hextool, libjansson4, libevent-2.0-5, cnee, psi-plus, mihphoto, shc
Maemo flasher/rescue live image.
Fremantle Harmattan SDK VM









So here it comes:
USB LAN Connection Windows 7 Internet from N900
Prerequirements usb lan:
[PC]
driver e.g. from madde
Connect a windows system with usb lan:
[N900] forwarding
In case you want forward/open ports to your pc
{for/out-ports}
Before you generate the rules and start the firewall script you need to put your pc ip, the port and protocol then push the add button.
N900: gpxsee, fahrplan, gpscon, genwall, qrcode, hextool, libjansson4, libevent-2.0-5, cnee, psi-plus, mihphoto, shc
Maemo flasher/rescue live image.
Fremantle Harmattan SDK VM
Last edited by Halftux; 2016-05-14 at 21:11. Reason: added link to driver